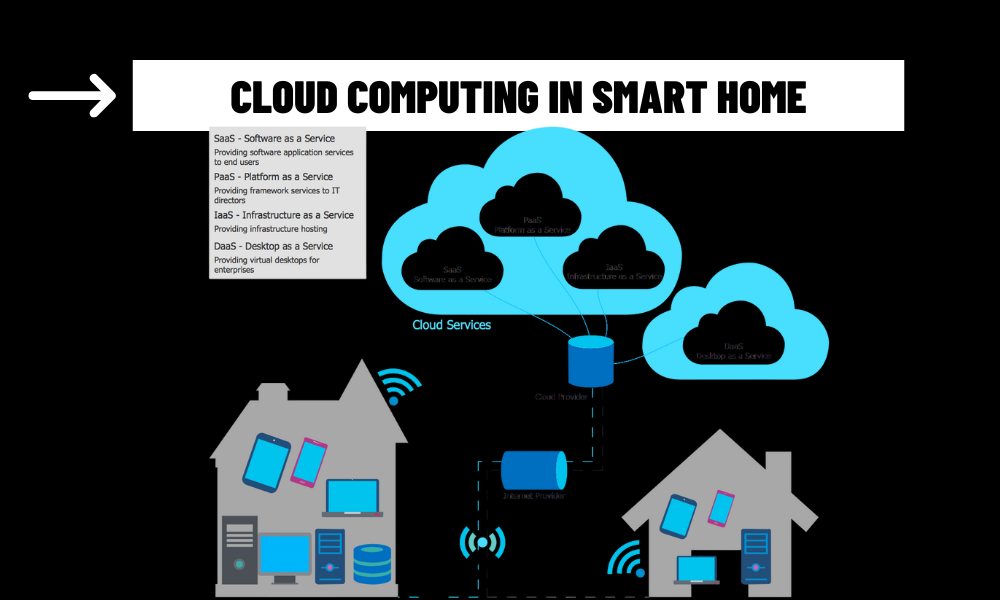
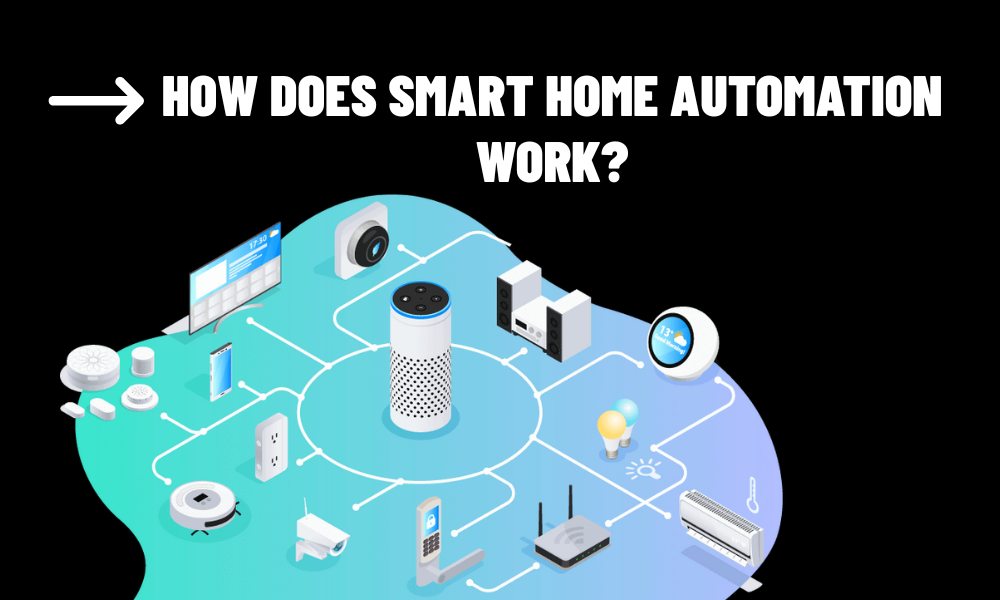
As smart homes become increasingly reliant on cloud computing, concerns about security and privacy have taken center stage. Cloud-based smart home systems store sensitive data, such as video feeds, voice commands, and user behavior patterns, on remote servers, making them potential targets for cyberattacks. This article examines the security and privacy implications of cloud computing in smart homes, best practices for safeguarding data, and strategies to balance functionality with user trust.
Contents
How Cloud Computing Enables Smart Home Security
Cloud computing enhances smart home security by providing:
Encrypted Communication: Data transmitted between devices and cloud servers is encrypted using protocols like TLS, ensuring that intercepted data remains unreadable.
Centralized Updates: Cloud platforms deliver automatic firmware and software updates to patch vulnerabilities, keeping devices secure without user intervention.
Scalable Monitoring: Cloud systems can process and analyze data from multiple security devices, such as motion sensors and cameras, to detect anomalies in real time.
For example, Arlo security cameras use cloud-based AI to distinguish between humans, animals, and vehicles, sending precise alerts to users via mobile apps.
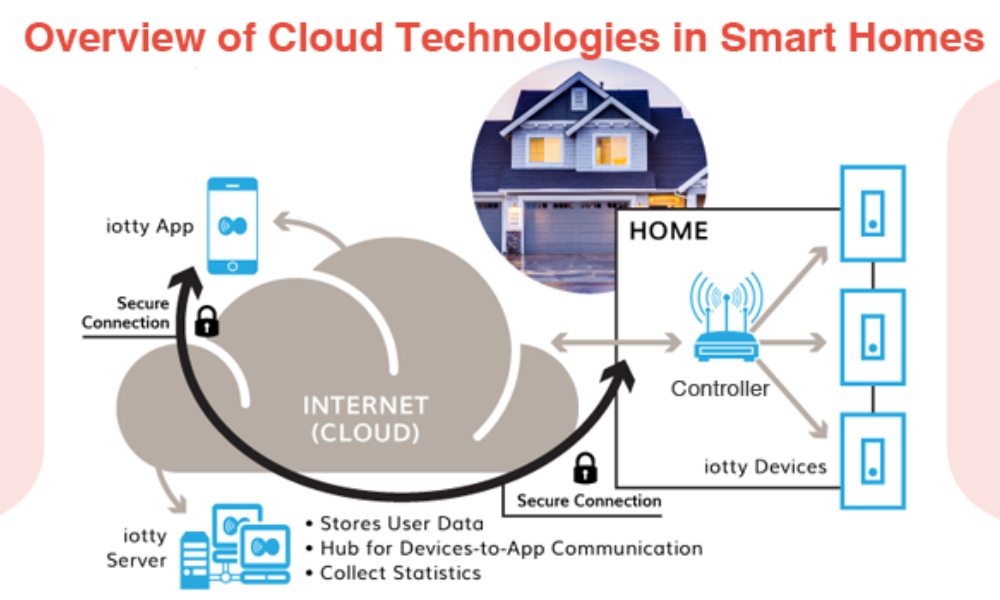
Privacy Risks in Cloud-Based Smart Homes
While cloud computing offers robust security features, it also introduces privacy risks:
Data Breaches: High-profile incidents, such as the 2021 Verkada camera hack, exposed vulnerabilities in cloud-stored video footage, underscoring the need for stringent security measures.
Data Monetization: Some companies may analyze or share user data for advertising purposes, raising ethical concerns about consent and transparency.
Voice and Video Recordings: Devices like smart speakers and doorbells often store recordings in the cloud, which could be accessed by unauthorized parties if not properly secured.
Best Practices for Enhancing Security and Privacy
To mitigate risks, manufacturers and users can adopt the following strategies:
End-to-End Encryption: Ensure that data is encrypted both in transit and at rest. Companies like Apple HomeKit emphasize local processing and end-to-end encryption to minimize cloud exposure.
Multi-Factor Authentication (MFA): Require MFA for accessing cloud-based smart home apps to prevent unauthorized access.
Regular Audits and Compliance: Manufacturers should conduct security audits and comply with standards like ISO 27001 or GDPR to protect user data.
User Control and Transparency: Provide clear privacy policies and options for users to delete stored data or opt out of data collection.
Hybrid Architectures: Combine edge and cloud computing to process sensitive tasks locally, reducing the amount of data sent to the cloud.
User Responsibilities
Consumers also play a critical role in securing their smart homes:
Strong Passwords: Use unique, complex passwords for smart home accounts and Wi-Fi networks.
Network Security: Secure home routers with WPA3 encryption and disable remote management features.
Device Selection: Choose devices from reputable brands with strong privacy policies and regular updates.
The Path Forward
The future of cloud-based smart homes depends on building user trust through robust security and privacy measures. Emerging technologies, such as blockchain for decentralized data storage and AI-driven anomaly detection, could further enhance protection. Additionally, regulatory frameworks are evolving to hold companies accountable for data misuse, encouraging greater transparency.
Cloud computing powers the functionality of smart homes but introduces significant security and privacy challenges. By implementing advanced encryption, transparent policies, and hybrid architectures, manufacturers can address these concerns while maintaining user convenience. As smart home adoption grows, collaboration between companies, regulators, and users will be essential to create a secure and trustworthy ecosystem.